How to improve the data reading rate of RFID system
Gabion,Gabion Wall,Gabion Cages,Gabion Wall Baskets Anping Xinghong Metal Wire Mesh Co.,Ltd , https://www.apironwire.com
This article will analyze the RFID system by introducing the basic components and working principles of the RFID system. Combining with the problems encountered in practical applications of RFID systems, and the reasons for the fact that the system read rate is not high due to factors such as the presence of blind areas in the reading range of the reader, excess data at different reading points, and mutual interference between readers, etc. Optimize the hardware configuration, improve the software design, play the role of middleware and integrate other technologies in four aspects to improve the RFID system data read rate.
1, the basic composition of the RFID system
The RFID system is composed of at least two parts, an electronic tag (E-Tag/Transponder, also called a smart tag) and a reader (Reader/Interrogator, also called a reader/writer).
The electronic tag is a data carrier of a radio frequency identification system, and the electronic tag is composed of a tag antenna and a dedicated chip for the tag. The electronic tags are divided into active tags, passive tags, and semi-passive tags according to the different power supply modes; they are divided into low-frequency tags and high-frequency electronics depending on the frequency. Labels, UHF RFID tags, and microwave tags; divided into * tags, linear tags, paper tags, glass tube tags, circular tags, and special-purpose shaped tags, depending on the package type; Active and passive tags.
The reader is a device for reading or writing electronic tag information, and can be designed into a variety of products depending on the specific use environment and requirements. The reader wirelessly communicates with the electronic tag through the antenna and can read or write the electronic tag identification code and memory data.
A typical reader includes a high-frequency module (transmitter and receiver), a control unit, and a reader antenna. Of course, when the RFID system is actually used, it needs the support of other hardware devices such as computers and software. Figure 1 shows a typical RFID system composition diagram. 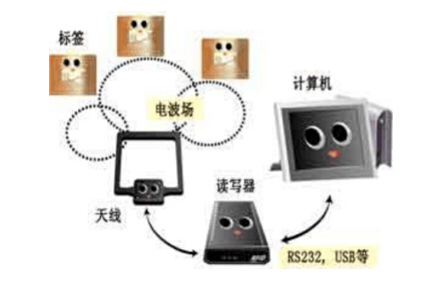
2. Basic Model of RFID System The basic model of the RFID system is shown in Figure 2. As a radio frequency carrier, the electronic tag and the reader implement a spatial (non-contact) coupling of a radio frequency signal through a coupling element. Within the coupling channel, energy transfer and data exchange are realized according to the timing relationship. 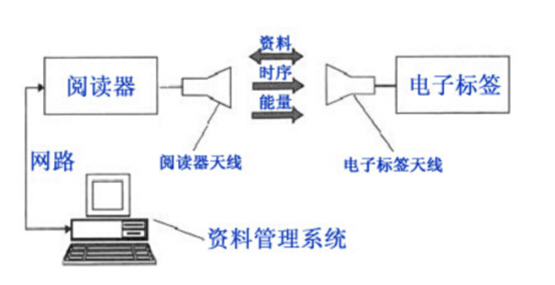
3, RFID system read rate issue to explore <br> <br> through the introduction of RFID system, we believe that the cause of the RFID system read rate is not high, mainly due to: a read range of the reader there blind, different reading points Excess data, readers interfere with each other, etc. In view of the above issues, we will explore the following four aspects.
3.1 Reasonable optimization of hardware configuration In terms of hardware, we must first clarify a problem. That's what your real 'requirements' are. Do not blindly believe that 'the price is higher, the larger the read range, the higher the frequency the better'. The so-called 'tailored', 'fit' one's own is the best. Based on this knowledge, you can choose hardware devices that match the actual needs.
At the same time consider all RFID tags and readers as a complete 'data network', so that a reasonable optimization of the hardware configuration, so that the entire system to maximize its effectiveness. Taking the access control system as an example, in order to prevent the read area of ​​the reader from having a blind area and causing a missed reading situation, the blind area may be compensated by increasing the number of readers or antennas to compensate for the blind area of ​​the reader reading range; The readers interfere with each other and may use spatially separate readers or antennas to avoid mutual interference. In addition, according to actual needs, by appropriately adjusting the antenna layout and antenna transmission power, the data reading rate of the RFID system can also be improved.
3.2 Improve software design At present, the hardware facilities of the optimized configuration of the RFID system can basically meet the needs of data read rate, and as the price of the reader decreases, end users can easily deploy a large number of readers in their application sites. It not only solves the missing reading problem, but also can obtain more useful information from these systems. But the new problem that comes with it is: extra data reading or cross data reading. A simple description of this problem is that 'a tag that shouldn't be read in a certain location is read by a reader that shouldn't read the tag'.
The core of the LV positioning logic is based on 'singling out the required read data from spatial locations while filtering out unwanted read data'. The result is that the correct and accurate tag position is extracted from the results obtained by all RFID readers. In short, LV positioning logic is a software algorithm based on eliminating redundant data readouts based on the data set residing throughout the reader system. For the problem of conflict between multiple readers due to overlap of working ranges, the Color wave algorithm gives a good solution.
For electronic tag conflicts, the tag anti-collision algorithm generally uses the classical ALOHA protocol in the high-frequency band. Use ALOHA protocol tags to avoid collisions by selecting a way to send information to readers at a random time. In UHF bands, tree bifurcation algorithms are used to avoid conflicts. In addition, other optimization settings can be made to the software. For example, in an e-ticket system, the scanner's scan interval can be worked by software that is designed to adjust the scan time adaptively. In the case of a large flow of people, the scanning frequency of the reader is accelerated through software control to prevent missed reading. In the case of a small amount of people flow, the scanning frequency can be relatively reduced, thereby avoiding the occurrence of redundant data. .
3.3 Play a role in middleware RFID middleware is at the nerve center in various RFID industry applications. RFID middleware is a Message-Oriented Middleware (MOM). Messages are sent from one program to another or multiple programs in the form of messages. RFID middleware acts as an intermediary between RFID tags and applications. From the application side, using a set of common application programming interfaces (APIs) provided by middleware, it can connect to readers and read tag data.
Therefore, even if database software or back-end applications storing RFID tag information is added or replaced by other software, even when the type of RFID reader increases, the application does not need to be modified. This not only effectively solves the data read rate problem, but also eliminates other issues such as the maintenance complexity of many-to-many connections. RFID middleware will have very good development prospects in the future in service-oriented architecture (SOA: Service Oriented Architecture Based RFID) and commercial information security applications.
3.4 Convergence of other technologies and sensor technologies In the next few years, an important application trend of RFID is the combination of RFID and sensors (such as sensors for measuring temperature and pressure), which have been implemented abroad. Due to the poor anti-interference of RFID, and the effective distance is generally less than 10m, it is a limitation on its application. Combining WSN (wireless sensor network) with RFID, utilizing the former's effective radius of up to 100m to form a WSID network, this will greatly offset the inadequacies of the RFID system itself.
Integration with WIMAX, 3G, GPS and other communication technologies WiMAX (Worldwide Interoperability for Microwave Access) is a simple definition of a wireless broadband data transmission system. WiMAX's wireless service range can be as long as several kilometers in the case of maintaining high data traffic in urban areas. Its performance far exceeds the existing wireless network technology. In the case of directional communication connections, the service range can maintain a certain amount of data traffic. Up to 50km, due to its extremely high performance, WiMAX technology is considered the best alternative for DSL UMTS connections.
The integration of WiMAX, 3G, GPS, and RFID is continuing to advance with the active participation of all parties. RFID tags have the characteristics of small size, large capacity, long life, and reusability. They can support fast read and write, non-visual identification, mobile identification, multi-target recognition, location, and long-term tracking management. The cost savings and efficiency improvements have prompted RFID technology to become an important entry point for informatization in various industries. They will build a wireless broadband network that can meet the needs of multiple application environments and generate rich applications, expanding the application of RFID technology.
Biometrics fusion with biometrics is a solution that uses automated techniques to measure physical or personal behavior characteristics for identity verification and compare these features or characteristics with database template data to complete the certification. The biometrics system captures samples of biological features. Unique features will be extracted and converted into numerical symbols that are saved as individual feature templates. People interact with the identification system and certify their identities to determine matches or mismatches. The commonly used biometric identification technologies include fingerprints, palm prints, human faces, speech, retina, signature recognition, and the like.
In short, the integration of RFID systems with other technologies is imperative, and great results have been achieved so far. It solves the problem of low data reading rate of RFID systems, and will inevitably make RFID technology widely used. It will eventually be as deep as the barcode technology and gradually extended to all aspects of the industry, which will play a key role in improving the operating efficiency and economic efficiency of the industry. The role of sex, thus promoting a new leap in the global economy, has a profound impact on human society.
4 Conclusion
As a whole, the development of RFID systems will become better and better in the future. Although there are still some technical and application issues such as low read rates, we believe that through hardware optimization, software design, and middleware The role and integration of other technologies and a series of measures to overcome the current problems of RFID is not difficult. Under the guidance of a strong market, RFID technology will inevitably cause a major change in the world. It will become a new economic growth point in the future and will eventually become the largest information technology support for the development direction of Chinese enterprises. It can be predicted that in the near future, as a global manufacturing base, China will be the world's largest RFID application market in the future. This will be a rare opportunity for domestic research institutions and enterprises.